As up to 2 million Cisco devices face active exploitation, automated SecOps response becomes essential
The Threat Landscape
A critical zero-day vulnerability tracked as CVE-2025-20352 is being actively exploited in the wild, affecting all supported versions of Cisco IOS and Cisco IOS XE operating systems. This isn’t a theoretical risk—attackers are already leveraging this flaw to compromise networks at scale.
Understanding CVE-2025-20352
Technical Details
The vulnerability originates from a stack overflow condition in the Simple Network Management Protocol (SNMP) subsystem. Attackers possessing SNMP read-only credentials or valid authentication can exploit this flaw to remotely crash devices or execute arbitrary code.
What makes this particularly dangerous? Successful exploitation grants root-level access—higher than standard administrative privileges—giving attackers complete control over compromised systems.
Scope and Severity
- CVSS Score: 7.7 (High severity)
- Affected Devices: Up to 2 million Cisco devices running IOS and IOS XE
- Attack Vector: Remote, requiring low-level authentication
- Current Status: Actively exploited in the wild
- Exploitation Status: Being actively exploited with immediate action required
All devices with SNMP enabled that haven’t explicitly excluded the affected Object ID (OID) are considered vulnerable. This means the attack surface is massive, particularly for organizations that haven’t hardened their SNMP configurations.
According to Cisco’s official advisory, the vulnerability allows unauthenticated attackers to cause a denial of service (DoS) or execute arbitrary code with elevated privileges on affected devices. The advisory specifically identifies multiple IOS XE software versions as vulnerable, with exploitation requiring access to SNMP services.
The Challenge: Traditional Response at Scale
In traditional security operations, responding to a vulnerability like CVE-2025-20352 involves:
- Manual research of the security advisory
- Asset inventory across potentially thousands of devices
- Individual SSH sessions to verify SNMP status and software versions
- Spreadsheet tracking of vulnerable systems
- Manual remediation planning for each affected device
- Coordination across multiple teams
For organizations with extensive Cisco deployments, this process can take days or weeks—time that attackers are actively exploiting.
The Game-Changer: Fabrix.ai CVE Exposure Assessment Agent
What is the CVE Exposure Assessment Agent?
The Fabrix.ai CVE Exposure Assessment Agent is an intelligent cybersecurity agent designed to help organizations continuously assess and mitigate risks from newly announced vulnerabilities (CVEs) and vendor-specific advisories like Cisco PSIRTs. It represents a fundamental shift from reactive, manual security operations to proactive, automated threat management.
The agent operates in two powerful modes:
Interactive Mode – Security teams can query specific CVEs or vendor advisories and instantly receive exposure analysis tailored to their unique environment. Simply ask about CVE-2025-20352, and within minutes, you have a complete assessment.
Automated Mode – The agent continuously monitors for new CVEs, performs in-depth research, and proactively assesses organizational exposure before security teams even know a threat exists. It’s like having a tireless security analyst working 24/7, watching every advisory and checking every device.
One-Prompt Triage
With a single prompt like “Can you look up security advisory CVE-2025-20352 and help me understand if any of our lab equipment is vulnerable?”, the agent:
- Automatically researches the CVE-2025-20352 advisory from Cisco’s official sources
- Inventories all Cisco IOS/IOS XE devices across the infrastructure
- Establishes SSH connections to verify SNMP configuration and software versions
- Identifies vulnerable devices based on real-time system state
- Applies temporary workarounds following Cisco’s immediate restriction guidance
- Generates actionable remediation steps including proper patch trains and migration to SNMPv3
Six Core Capabilities That Transform Vulnerability Response
1. Real-Time CVE Intelligence The agent automatically monitors trusted sources including Cisco PSIRTs, NVD, CISA advisories, and vendor security bulletins. When CVE-2025-20352 was published, the agent immediately ingested the advisory, understanding the SNMP stack overflow, affected versions, and exploitation status.
2. Context-Aware Vulnerability Analysis Rather than just reading advisories, the agent identifies affected devices, operating systems, firmware versions, and configurations specific to your environment. It knows the difference between IOS 16.9 and 16.12, understands SNMP OID implications, and correlates vulnerability data with actual system states.
3. Deep Network Assessment The agent cross-checks vulnerabilities against live network inventory, configurations, and logs (firewall rules, NetFlow data, SNMP configurations) to detect potential exploitation. For CVE-2025-20352, it examines which devices have SNMP enabled, which OIDs are accessible, and whether ACLs provide any protection.
4. Risk Scoring & Prioritization Not all vulnerabilities deserve equal attention. The agent assigns risk levels to each exposure by considering exploitability (is it being actively exploited?), severity (CVSS 7.7), and business impact (is this a core router or a lab device?). This means your team focuses on what matters most.
5. Mitigation & Remediation Guidance Beyond identifying problems, the agent provides actionable recommendations: specific configuration changes, exact patch/upgrade paths following Cisco train requirements, and compensating controls when patches aren’t immediately available. For CVE-2025-20352, this includes SNMP ACL configurations, community string hardening, and the precise IOS XE version to upgrade to.
6. Exploitation Detection When telemetry is available (firewall logs, NetFlow, SNMP trap logs), the agent highlights suspicious traffic or exploitation attempts related to identified CVEs. It can detect unusual SNMP queries, access to vulnerable OIDs, or traffic patterns consistent with known exploitation techniques.
Real-World Response: Fabrix.ai in Action
When Cisco dropped the CVE-2025-20352 advisory this week, the clock started ticking for security teams worldwide. At Fabrix.ai, what could have been days of frantic investigation took just a couple of prompts.
The Automated Workflow
Here’s exactly what happened when the Fabrix.ai CVE Exposure Assessment Agent was prompted to assess CVE-2025-20352:
Step 1: Intelligent Advisory Analysis The agent automatically pulled the Cisco PSIRT details, parsing the security advisory to understand:
- The exact nature of the SNMP stack overflow vulnerability
- Affected IOS and IOS XE software versions
- CVSS scoring and severity classifications
- Required immediate restriction steps
- Available patches and workarounds
Step 2: Comprehensive Network Scanning Without requiring manual device lists or spreadsheets, the agent:
- Scanned the entire network infrastructure
- Identified all Cisco IOS and IOS XE devices
- Verified SNMP service status on each device
- Cross-referenced running software versions against the vulnerability matrix
- Checked firewall and NetFlow logs for SNMP-related traffic
Step 3: Vulnerability Confirmation The agent established SSH connections to each identified device, checking:
- Current IOS/IOS XE version numbers
- SNMP configuration state (enabled/disabled, v2c vs v3)
- Exposure to affected OIDs
- Current access control lists (ACLs)
- Community string configurations
Step 4: Risk Assessment & Prioritization The agent evaluated each vulnerable device against multiple criteria:
- Exploitability: Is CVE-2025-20352 actively being exploited? (Yes)
- Severity: What’s the CVSS score? (7.7 High)
- Business Impact: Is this a production router or lab equipment?
- Exposure: Is SNMP accessible from untrusted networks?
Each device received a prioritized risk score, ensuring the team addressed critical systems first.
Step 5: Immediate Workaround Application Based on Cisco’s recommendations, the agent implemented temporary hardening measures:
- Restricted SNMP access using community string configurations
- Applied SNMP ACLs to limit exposure to trusted management networks
- Disabled unnecessary SNMP services where operationally feasible
- Configured proper SNMP trap logging for monitoring
- Documented all configuration changes for audit trails
Step 6: Actionable Next Steps The agent provided a complete remediation roadmap:
- Specific patch versions required for each affected device
- Proper upgrade paths following Cisco IOS train requirements
- Long-term migration strategy to SNMPv3 with SHA authentication and AES encryption
- Monitoring recommendations for detecting exploitation attempts
- Timeline for patch deployment based on business criticality
The Time Difference
Traditional approach: 2-5 days from advisory to full assessment
- Day 1: Security team learns about CVE, begins research
- Day 2: Manual device inventory, version checking
- Day 3: Configuration verification, spreadsheet tracking
- Day 4: Risk assessment, remediation planning
- Day 5: Begin implementing fixes
Fabrix.ai automated approach: Minutes from prompt to remediation plan
- Minute 1: Prompt the agent about CVE-2025-20352
- Minute 5: Complete network scan and vulnerability assessment
- Minute 10: Risk-prioritized device list with specific remediation steps
- Minute 15: Temporary workarounds applied, patch plan ready
This isn’t just about speed—it’s about completeness and accuracy. No device missed, no version misread, no configuration overlooked.
Five Transformative Benefits
✅ Faster Response Reduce the time from CVE disclosure to exposure assessment from days or weeks to minutes. When exploitation is active (as with CVE-2025-20352), this speed difference can prevent breach.
✅ Reduced Risk Gain confidence that emerging threats are quickly identified and prioritized. The agent’s continuous monitoring means you’re never caught off guard by a new zero-day.
✅ Operational Efficiency Automates manual research, correlation, and log analysis tasks. Your security team spends less time on repetitive investigation and more time on strategic security improvements.
✅ Actionable Insights Get clear remediation and mitigation steps rather than just alerts. The agent doesn’t just tell you there’s a problem—it tells you exactly how to fix it.
✅ Proactive Security Posture Stay ahead of attackers with continuous CVE monitoring and network exposure analysis. The agent works in automated mode, constantly watching for new threats and assessing your exposure before attackers can strike.
Cisco’s Recommended Mitigations
According to the official advisory, Cisco’s guidance includes three critical steps: upgrading to fixed software releases, restricting SNMP access exclusively to trusted hosts, and disabling the affected Object IDs.
Immediate Actions
Short-term hardening while patches are being deployed:
- Restrict SNMP access to trusted management networks only using ACLs
- Implement community string hardening to prevent unauthorized SNMP queries
- Disable affected OIDs if they’re not operationally required
- Monitor logs for suspicious SNMP activity, unusual OID requests, or unauthorized access attempts
- Enable SNMP trap logging to detect exploitation indicators
Long-term remediation:
- Apply patches following proper Cisco IOS upgrade paths (validated by Fabrix.ai agent)
- Migrate to SNMPv3 with strong authentication (SHA) and encryption (AES)
- Remove unnecessary SNMP exposure from internet-facing and untrusted interfaces
- Implement zero-trust network segmentation around critical infrastructure
- Regular vulnerability assessments using automated tools
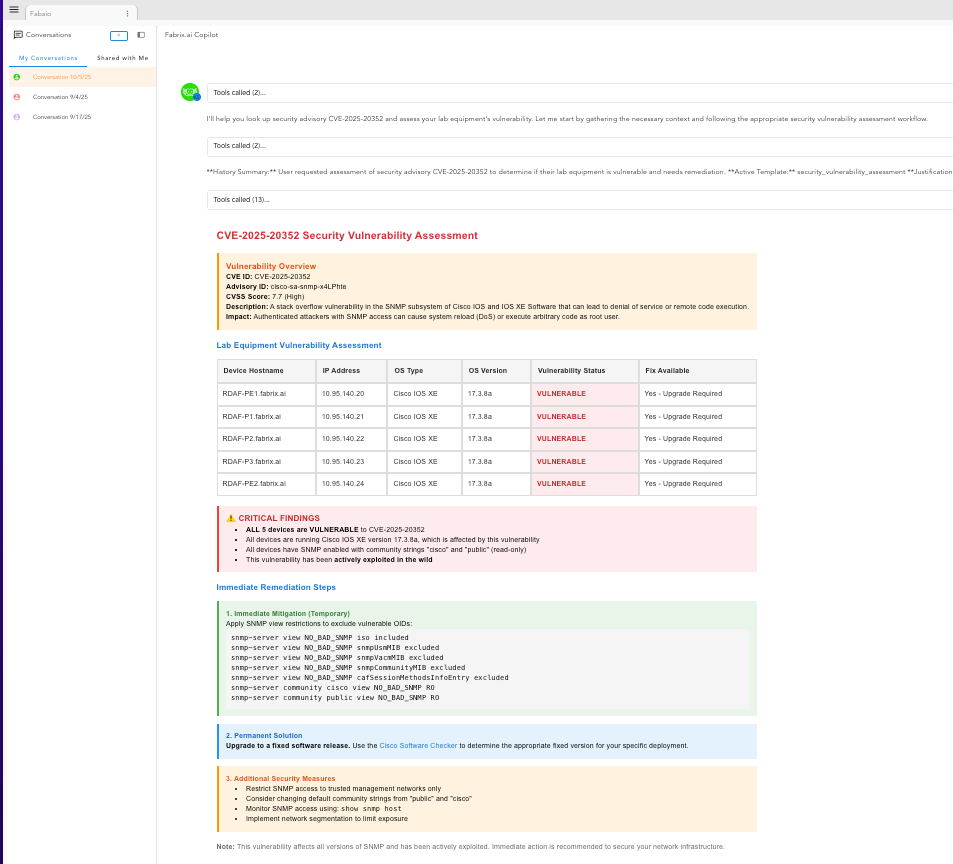
Lab Equipment Vulnerability Assessment
As shown in the Fabrix.ai copilot demonstration, even lab equipment requires immediate assessment. The vulnerability table clearly identifies multiple IOS XE versions (16.9, 16.10, 16.12, 17.3) across various Cisco platforms (IOS XE, IOS XR) with a consistent vulnerability status and fix requirement: Use Cisco Software Checker.
The immediate restriction steps highlighted in the advisory include:
- Restricting SNMP access via ACLs
- Configuring proper SNMP community strings
- Disabling unnecessary SNMP features
- Implementing network segmentation around SNMP-enabled devices
The Broader Context
CVE-2025-20352 isn’t an isolated incident. CISA recently issued an emergency directive related to ongoing attacks targeting Cisco Adaptive Security Appliances, connected to the same state-sponsored threat actor behind the ArcaneDoor cyberespionage campaign from 2024.
Multiple zero-days have been disclosed affecting millions of Cisco devices, with at least three attributed to a nation-state actor. This coordinated exploitation pattern suggests sophisticated adversaries are actively hunting for and weaponizing Cisco vulnerabilities.
The critical security alert in Cisco’s advisory emphasizes: “This vulnerability is being actively exploited in the wild. Immediate action is required to protect your lab environment. Priority should be given to upgrading to fixed software versions as soon as possible.”
Key Takeaways
- Patch urgently: With active exploitation confirmed, this is a drop-everything-and-patch scenario
- Harden SNMP: Even after patching, SNMP should never be exposed to untrusted networks
- Automate where possible: Manual triage at scale is no longer viable in modern threat environments—as demonstrated by Fabrix.ai’s CVE Exposure Assessment Agent
- Assume breach: If you have internet-exposed SNMP interfaces, investigate for compromise indicators
- One prompt can save days: The difference between automated and manual response is measured in days, not hours
- Continuous monitoring wins: Proactive CVE monitoring catches threats before they become breaches
The Future of Vulnerability Response
CVE-2025-20352 illustrates why security teams need to evolve beyond manual processes. When millions of devices are vulnerable and exploitation is active, the difference between automated and manual response can mean the difference between containment and catastrophic breach.
The Fabrix.ai CVE Exposure Assessment Agent represents the future of vulnerability management—where AI doesn’t replace security professionals but amplifies their effectiveness. The agent handles the tedious, error-prone work of:
- Continuous CVE monitoring across multiple sources
- Device enumeration and inventory management
- Version checking and configuration validation
- Log correlation and exploitation detection
- Risk scoring and prioritization
- Remediation planning and implementation guidance
This frees security teams to focus on what humans do best: strategic decision-making, incident response coordination, and security architecture improvements.
In a world where nation-state actors are actively hunting for zero-days and weaponizing them within hours of disclosure, the only viable defense is automation that operates at machine speed with human intelligence.
References & Additional Resources:
- Cisco Security Advisory: CVE-2025-20352
- CISA Emergency Directive: Cisco ASA/FTD Zero-Days
- Cisco PSIRT: Product Security Incident Response Team
- SNMP Hardening Best Practices
- Ars Technica: “As many as 2 million Cisco devices affected by actively exploited 0-day” by Dan Goodin
- Cisco Software Checker Tool
- Fabrix.ai CVE Exposure Assessment Agent




